
Salesforce is a powerful cloud-based CRM platform that helps businesses of all sizes manage their customer relationships, sales, and marketing. It’s also one of the most secure platforms available, with a wide range of features and tools to help businesses protect their data.
In this blog post, we’ll take a comprehensive look at Salesforce security, including:
- What is Salesforce Security?
- The different layers of security that Salesforce has in place
- The security features and tools that are available to Salesforce users
- Best practices for implementing and maintaining Salesforce security
What is Salesforce Data Security?
Salesforce data security involves safeguarding information stored within Salesforce platforms. It encompasses measures to protect data from unauthorized access, ensuring its confidentiality, integrity, and availability. This includes controlling user permissions, encrypting sensitive data, setting up firewalls, and monitoring access to prevent breaches. The aim is to maintain data privacy, comply with regulations, and prevent data loss or leaks. Salesforce data security strategies focus on fortifying defenses against cyber threats, securing data throughout its lifecycle within the Salesforce environment, and preserving the trust and confidentiality of critical business information.
Layers of Salesforce security


Salesforce security is built into every layer of the platform, from the infrastructure to the application. This includes:
1) ORGANIZATIONAL LEVEL SECURITY
- Organization level security is the highest level of security in salesforce, it includes maintaining a list of authorized users, set password policies, and limit logins to certain hours and locations.
- It decides where and when can user access the system.
- It secures data from any unauthorized user.
- Important security features in this level are
i] IP restriction
ii] Password policies
iii] Login access



2) OBJECT LEVEL SECURITY
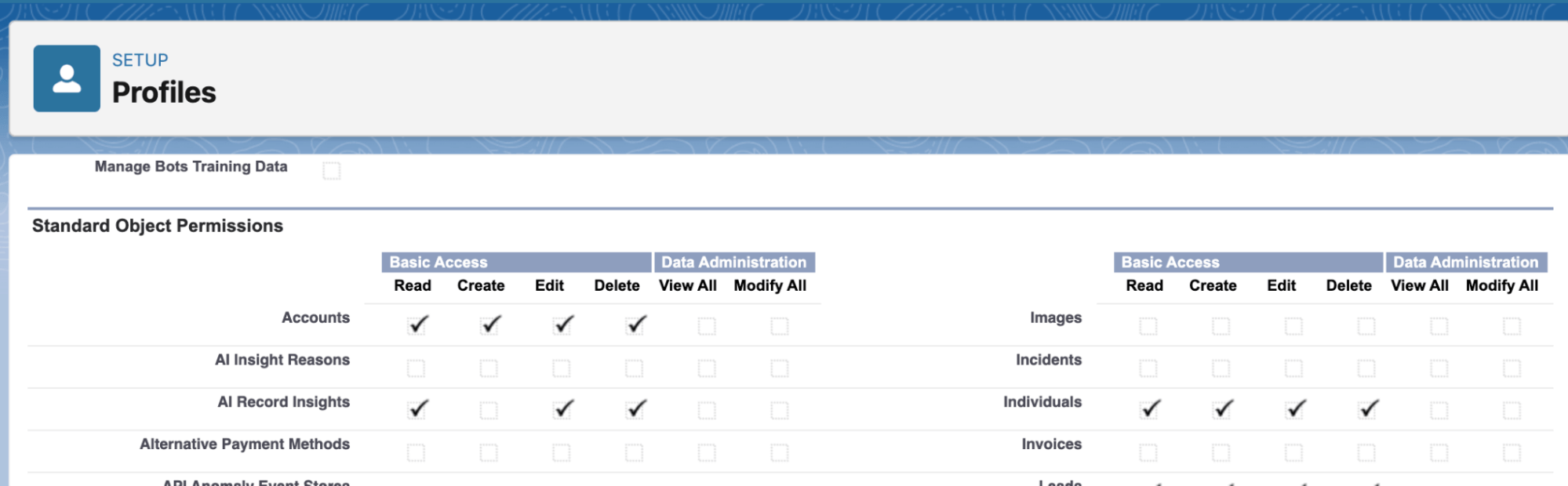
Object-level Security is used to control data access. Using object Permissions. You can prevent a user from seeing, Creating, Editing Or Deleting any instance of a particular object types, such as a lead or opportunity object. You specify object permissions in permission sets and Profiles. Permission sets and profiles are collections of settings and Permissions that determine what a user can do in the application.
There are two ways to set object permission are as:
- Profiles – Profiles are collections of settings and permissions that determine What a user can do in the application.
- Permissions Set – A permission set is a collection of settings and Permissions that give access to users to various tools and functions.
3) FIELD LEVEL SECURITY
Field level security in Salesforce is configured for a User’s profile. Using a Field Level Security administrator can Control whether a user can create, see, update, and Delete(CRUD) the value for a particular field on an object.

4) RECORD LEVEL SECURITY
Record level Security allows particular users to view an Object, but then restrict the individual object records They’re allowed to see. You can manage record-level access In these four ways:
- Organization-wide defaults
- Role hierarchies
- Sharing rules
- Manual sharing
Read More: Top-5 Salesforce Security Best Practices
Conclusion
Security remains a top priority for Salesforce, being a crucial cloud application. Any lapses in security or data breaches can lead to substantial business disruptions and harm your reputation. This security guide offers actionable recommendations to fortify your security measures, ensuring compliance with regulations.
For assistance in securing your Salesforce setup or implementing Salesforce Shield, don’t hesitate to contact us. Benefit from a complimentary consultation with our Salesforce security professionals to safeguard your system.













